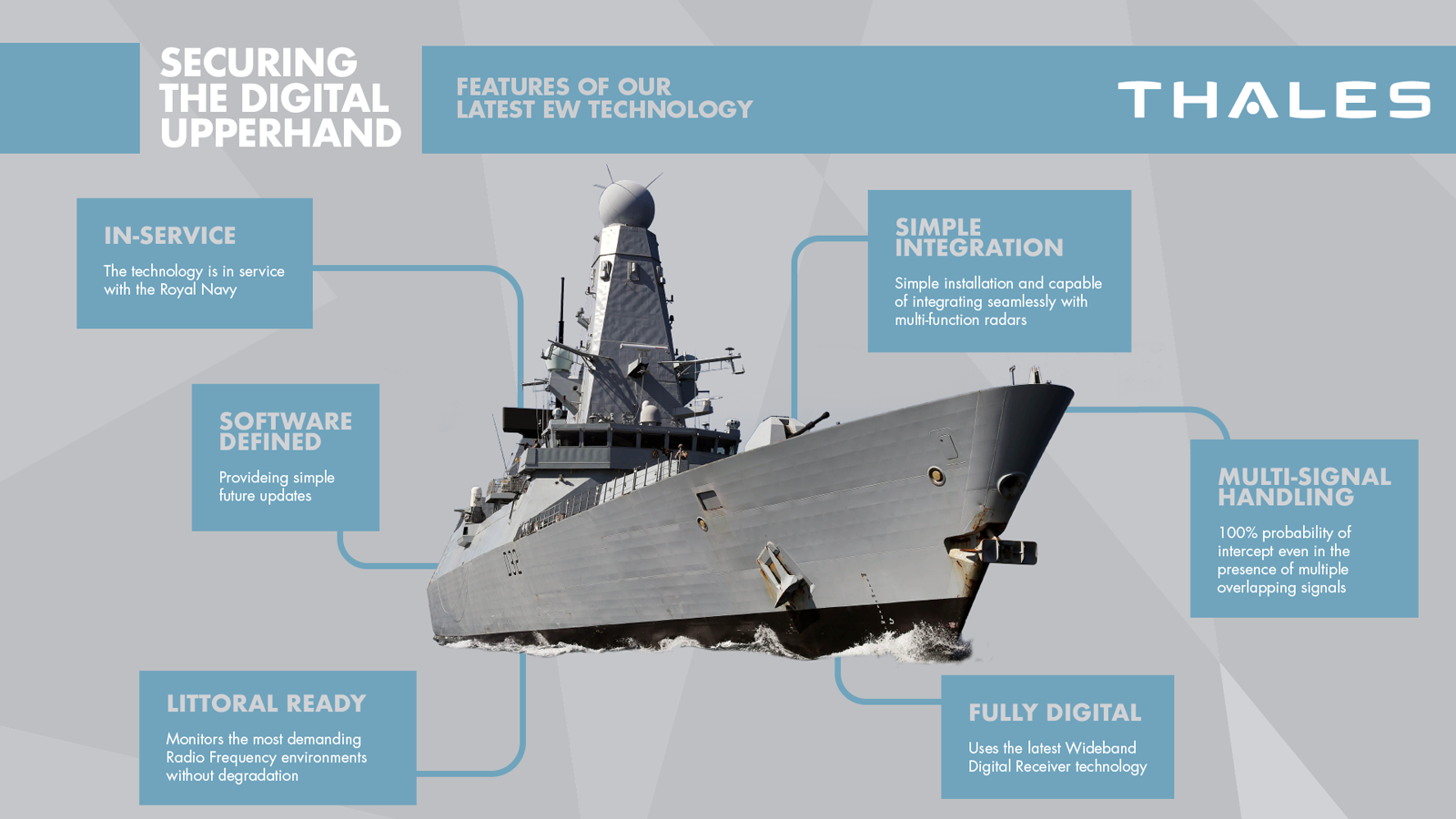
Securing the digital upper hand in Electronic Warfare
Thales UK is a world leader in the development of Electronic Warfare (EW) technology, having created the world’s first digital wideband solution, that has helped to save the lives of the military and the public all over the world.
The company’s approach to innovation, paired with its ability to listen and respond to customer’s needs, has enabled Thales to become the Royal Navy’s principal provider of EW equipment for over 60 years.
The end of Gulf War One in 1991, marked a pivotal moment in the relationship between Thales and the Royal Navy.
At the time, the British and American Navy had been using EW technology to patrol the 120 mile Shatt Al-Arab river that borders Iran and Iraq, to monitor whether United Nations Security Council sanctions were being implemented.
Phil Ventress, who was Head of Royal Navy EW Operational Training before he joined Thales in 2001, visited the Gulf to monitor the fleets performance.
To his alarm, he found that the EW equipment was starting to suffer from saturation.
“I had to tell the ships to turn half of their aerial system off on the non-threat side because increasing levels of civilian and military signal incursions that were visible on the spectrum were becoming too much for the equipment,” said Ventress.
Just a few years previously the American ship USS Stark was patrolling waters in the region when it was hit by two missiles that were fired from an Iraqi aircraft. EW equipment had not picked up the impending threat and 37 sailors died.
“Threat detection was becoming increasingly difficult and something had to be done before a similar tragedy occurred. We had to do something radical,” said Ventress who served in the Royal Navy for 27 years.

‘We had to do something radical’
Thales UK undertook the Daphne Research and Development Programme with the Ministry of Defence (MOD) in 2004 in response to the Navy’s requirements.
The programme was a bold leap into something no one even knew was possible - Full-Spectrum Wideband Digital for EW. It changed the history of EW forever.
When Ventress joined the Navy in 1974, there were only a couple of channels available for operators to listen to and they worked at a receiver bandwidth of either 100 megahertz or 250 megahertz analogue.
By 1982, EW capabilities could see from 2 to 18 gigahertz, but the technology was analogue.
The mid 1990s, saw the bandwidth increase from 0.5 up to 40 gigahertz. However, the analogue equipment began to struggle with the increasing numbers of incursions on the spectrum. This meant that operators were unable to hear signals properly when they tried to tune into radio waves that they knew were there.
The late ‘90s into early 2000 saw narrowband digital windows conceived. They acted like little periscopes, or windows of light that operators could look down for a clear signal. This meant that you could hear the three or four channels that were digitised really clearly, but only one at a time.
By 2010, Thales had digitised the whole frequency range with Digital Wideband capabilities that are representative of the technology we have today. The technology is the equivalent of being able to tune into any radio station from the DAB radio in your car from the click of a button.

Working in partnership with the UK MOD
Identification has also improved said Ventress who is now Head of Strategy and Product Policy at Thales.
“We are trying to get to the nirvana of 100% of identification automatically without a person being in the loop but that is extremely difficult to do because there are so many people accessing the spectrum.
“Currently, we have radars that can analyse about five million pulses per second, which gives you some understanding of the density of the signal environment that we are dealing with and the amount of processing power that is needed,” he said.
In 2012 Thales UK accepted a contract with the UK MOD to upgrade the surface fleet of the Royal Navy with a new Fully Digital Radar Electronic Support Measures (RESM) system, VIGILE-D featuring a unique digital antenna.
The six-year, multi-million pound research programme resulted in the development of radio frequency sampling and wideband digital receiver technology – which means a complete digital solution from antenna to console.
Digitising the radio frequency signal at the antenna, means that the majority of the receiver functionality is implemented using software and firmware algorithms.
This enables Thales to utilise commercial off-the-shelf hardware, which is cheaper to purchase and easier to maintain, alongside world leading EW support and emitter identification software.
Remaining one step ahead
Thales’ system, VIGILE-D, which has been awarded world patent rights, provides excellent performance in the dense radar environment, with the capability to manage multiple, simultaneous signals.
This makes it the most cost effective, technology advanced RESM solution available and enables customers to benefit from greater situational awareness, threat identification and intelligence gathering capability.
Ventress, said: “If you imagine, even in the early 2000s, we were still all watching football on our analogue TV sets and on a foggy night in Wigan, you could barely make out the white lines on the pitch. That is where we were. Now, we can see the sweat on Harry Kane’s brow through our HD televisions. That is the leap we have made. We have gone from analogue, to wide band, to digital wideband.”
Other countries like America are making the move to digital, however, they are working in a different way by taking lots of little narrowband 500 megahertz digital receivers and stacking them on top of each other to make 16 gigahertz. However, the amount of equipment needed for this approach means that the systems are big, heavy, hot, power hungry and costly.
By comparison, Thales has managed to define the spectrum purely in software, which means that its technology is small, lightweight and relatively inexpensive for the vast capabilities of the product.
This has helped to ensure that Thales’ customers are able to remain one step ahead of the rapidly evolving operational environment and can make better, more informed decisions.
For more information on our Electronic Warfare capabilities visit our webpage or contact:
Electronic Warfare UK Contact
Steve.towers@uk.thalesgroup.com
Electronic Warfare International Contact
richard.seltzer@uk.thalesgroup.com