The IoT is set for extraordinary growth, with a predicted 5.4 billion cellular IoT connections by 2028 (Ericsson Mobility Report, October 2023).
To reach this figure, there is a clear opportunity for everyone involved in the IoT ecosystem to leverage widely deployed and field-proven networks.
There's more.
The new generation of 5G networks is a tremendous asset for 5G IoT, helping to enable an explosive increase in the number of devices connected to people and each other.
But there's an itch.
IoT SAFE - The mobile industry's specs to securely deliver at scale
The emergence of billions more connected IoT devices presents profound security challenges for IoT service providers to protect sensitive data.
In response, the GSMA specifications (the IoT SAFE initiative) are being introduced to address the cyber security of the IoT.
All this by leveraging the IoT SIM card: the industry-recognised tamper-resistant elements of eSIM, SIM and, more recently, iSIM.
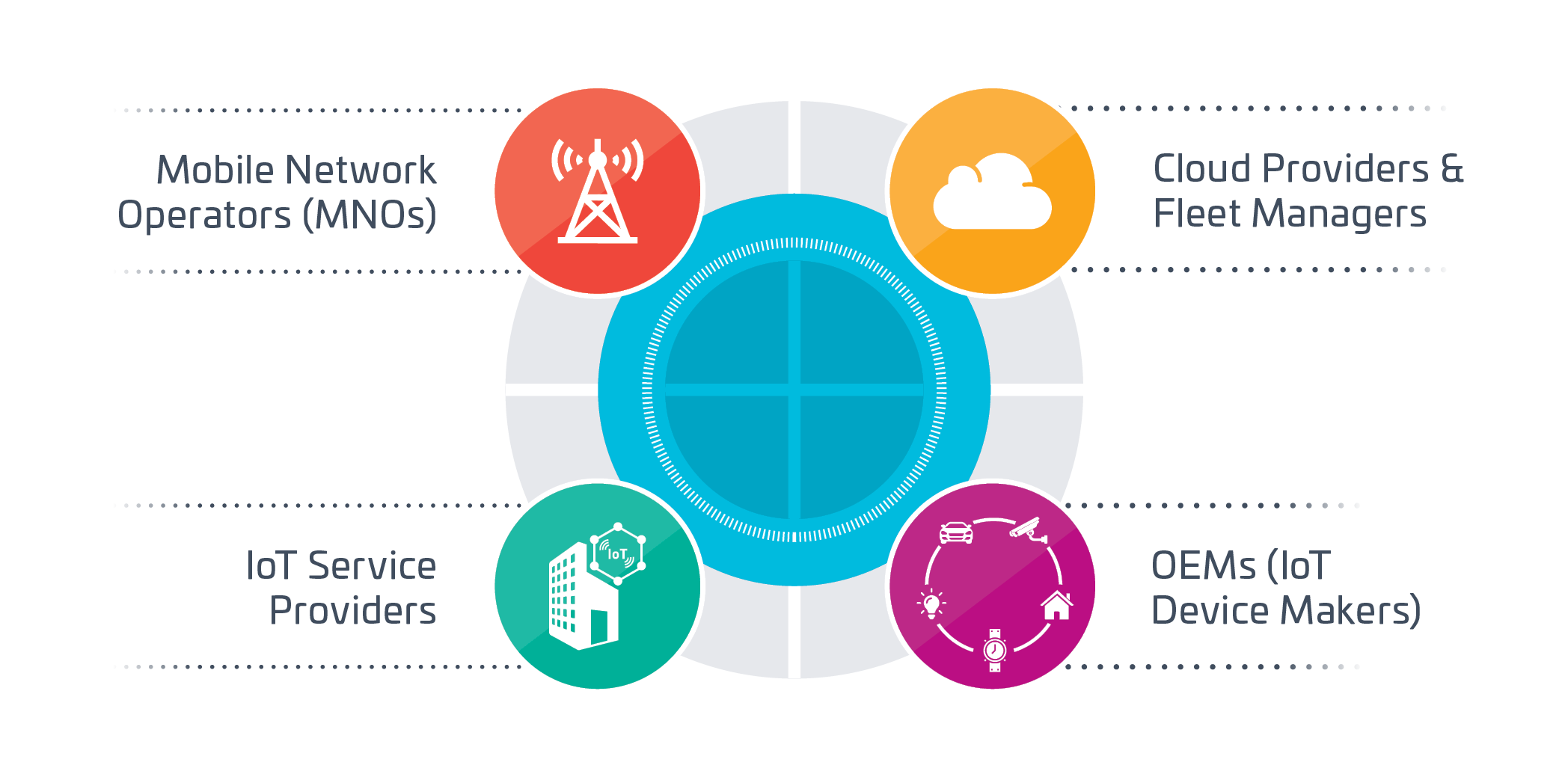
The key stakeholders in the cellular IoT ecosystem
- Mobile network / Telecoms operators - preparing for significant new commercial opportunities by providing the connectivity that embraces not only billions of people but also billions of device
- IoT Service Providers - developing applications for clouds and devices, managing fleets
- Public Cloud Providers - hosting and managing IoT applications and credentials
- OEMs - building IoT devices
Within the IoT ecosystem, devices collect, process and send data to the cloud, where various IoT applications are executed.
But while the emergence of billions more IoT devices creates a wealth of new opportunities for stakeholders, it also presents profound security challenges.
Increasing IoT attacks
The volume of IoT attacks is skyrocketing, doubling in six months according to a Kaspersky analysis: 1.5 billion IoT attacks were conducted in H1 2021, up from 639 million in H2 2020. When the United States showed more maturity in 2022, Africa, the Middle East and Turkey experienced a 659% increase in attacks in Q3 2022 vs Q3 2021.
To address these threats, the cloud platform for IoT must have absolute trust in the data received from IoT devices.
This trust is only possible by ensuring that both the device and the server are mutually authenticated (i.e. the device knows it is sending its data to the correct server, and the server knows it is a genuine device which requests data to be sent).
However, the IoT is characterised by fragmentation regarding the OS and chips employed.
An array of open-source and proprietary IoT OS is already on the market.
The result?
Proprietary IoT security solutions will not be able to scale or be duplicated.
Count on the SIM
The critical challenge is, therefore, how the device middleware can leverage the security services embedded in tamper-resistant elements in a scalable manner.
This is the problem that the GSMA IoT SAFE initiative solves by specifying an API so the IoT device middleware can use the credentials and security services in the SIM card for IoT, namely iSIM, eSIM or SIM, in a standardised manner.
In short, the solution is to utilise hardware tamper-resistant elements to secure IoT applications by design.
Securing the TLS handshake
The foundation of IoT cyber security is the TLS handshake protocol between the IoT device and the IoT cloud. It ensures that mutual authentication is enabled before any data exchange occurs.
Specifically, this process is achieved through hardware tamper-resistant element-based security and cryptography and GSMA IoT SAFE specifications.
SIM/eSIMs are ideally suited for IoT security.
Hardware tamper-resistant elements are a standard technology that integrates the new GSMA IoT SAFE specifications.
They deliver scalable 'security by design' for the IoT, meeting the scalability requirements of an IoT security framework by utilising standardised and field-proven SIM/eSIM technology, irrespective of form factor, and leveraging the multitude of devices already deployed in the field.
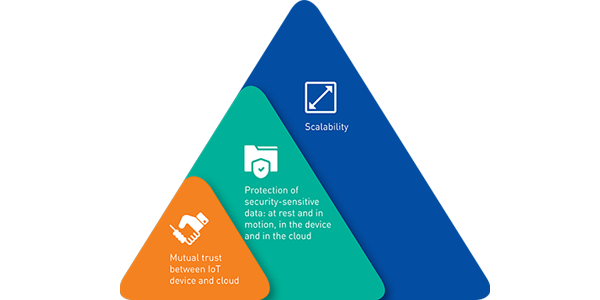
Hardware tamper-resistant elements address the three essential IoT security requirements:
- Mutual trust between the IoT device and the cloud
This end-to-end mutual authentication enables a TLS connection - Protection of data at rest and in motion
Data integrity
Data confidentiality - Scalability
There are already billions of Secure Elements in the field
Hardware tamper-resistant elements deliver scalable trust for IoT applications.
They act as the root of trust / cryptographic toolbox, based on tamper-proof hardware that stores private keys, digital certificates and security services.
Documents

How to Measure IoT Success?
Download the report
The IoT Now Guide to IoT Security 2022
Discover how recent developments in IoT SIM security can enhance cybersecurity and massive IoT deployments. A document from IoT Now Magazine.
Read more
Addressing IoT Cyber Security through eSIM-based Scalable Trust
Download the report
Connecting Wireless Data Deploying IoT Everywhere
Don’t miss the latest report of Beecham on the acceptance of eSIM in the IoT Market, based on survey of 412 IoT Suppliers and Solution Providers.
Download the report
Thales IoT SAFE delivers scalable trust for IoT applications
Infographic
Thales IoT SAFE delivers scalable trust for IoT applications [PDF - 182kb]Download the whitepaper
10 things you should know about the latest “Global Mobile Trends 2023” report where you will find highlights on 5G deployment, satellites and non-terrestrial networks, Private networks, the enterprise vertical stories: IoT 2.0, eSIM and the drive to scale, among many other impacting trends.
2024: the Year of eSIM unleashed? a Thales perspective
Don't miss the enlightening interview between Thales and Kaleido Intelligence, where they dive deep into the world of eSIM for consumers and IoT. Discover invaluable insights into the cutting-edge developments of eSIM and iSIM, the crucial factors that unlock the true potential of IoT, and Thales' visionary roadmap for empowering the industry in the years ahead. Don't wait, seize this opportunity to stay at the forefront of IoT innovation.
5 things you should know about breaking Barriers with eSIM in 2023
Watch the interview of Thales by Kaleido Intelligence, addressing eSIM for consumers and IOT
Interview on the fast growing eSIM market for the IoT
Stephane Quetglas, Marketing Director for eSIM and IoT Services at Thales and Tim Hatt, Heard of Research & Consulting at GSMA Intelligence &talk about the fast growing eSIM market for the IoT.
The control of IoT security risks in the Industry
IoT solutions are becoming increasingly important to business operations. So, inevitably, there are solutions that are becoming larger, more business-critical and far-reaching.
In this podcast, Stephane Quetglas, Marketing Director for eSIM and IoT Services and IoTNow’s host Jeremy Cowan are talking about IoT cyber security

Hardware tamper resistant elements deliver scalable trust for IoT applications
Hardware tamper resistant elements deliver scalable trust for IoT applications
Connected Drones
The central role of Mobile Network Operators in the commercial drone market
Connected Drones [PDF - 3mb]ScaleFlyt Remote ID & tracking for safe drone operations
Thales’s ScaleFlyt Remote ID is a brand new innovation that provides secure identification and tracking information of a drone in flight for UTM providers, airspace managers, UAV operators and ground observers. Delivering a trusted solution for a safer sky, ScaleFlyt Remote ID is technology that will contribute to enabling safe and secure large-scale drone operations.
Our IoT cybersecurity solutions
We can address the challenge of securely and efficiently connecting IoT devices to clouds through cellular networks, offering demonstrable benefits for all key stakeholders.
Specifically, we enable the opportunity to leverage assets that include widely deployed and field-proven cellular networks and Secure Element-based security solutions that store credentials, to deliver services that can be enhanced to address IoT security in an interoperable environment defined by GSMA IoT SAFE specifications.
We proactively lead the creation of new specifications, collaborating with the GSMA and other vital industries to facilitate streamlined deployment of IoT security and offer THALES' advanced implementation of the GSMA IoT SAFE initiative.
We are the world leader in OTA (Over The Air) platform solutions that enable credential life cycle management.
Need more information on scalable security for the IoT?
Are you interested in a proof of concept?
Contact us:
Thales Wins Gold for Best Cellular IoT Initiative
Guillaume Lafaix, VP Mobile Connectivity Solutions at Thales
Analysts expect an impressive growth of connected objects; among them, many will be connected to cellular networks. Telecom Operators have a crucial role to play
in the development of cellular IoT. In particular, they can significantly contribute to security. Discover how our award-winning cellular IoT service helps them achieve scalable and sustainable security for IoT in a cost-effective way.
Read the interview