Empowering the IoT Journey with Thales Solutions

Welcome to Thales Solutions for IoT, where you can now simplify, orchestrate, and secure your IoT landscape case.
Our mission is to drive the digital transformation of businesses with secure, robust, and scalable IoT connectivity.
As we gear up for a future with 2.5 billion new IoT devices by 2027, Thales stands ready with a strategic blueprint:
- Build: Partnering for design excellence with OEMs and IoT providers.
- Run: Streamlining your deployment with efficiency at the forefront.
- Protect: Ensuring the cybersecurity shield is always up and defending.
BUILD
Range of industry grade, standardized, futureproof hardware to securely connect devices.
RUN
Connectivity Suite enabling a secure, global, resilient, cost-effective connectivity from production to operation.
PROTECT
Cyber Protection Suite to protect IoTdevices and data from factory to the field, from edge to cloud.
Our Thales IoT Suite is your one-stop shop for securing and simplifying IoT connectivity, giving you the edge to lead in digitalisation.
Let's dig in.
The Build Phase: Crafting Reliable Connectivity
When creating cellular IoT devices, OEMs and service providers face various challenges.
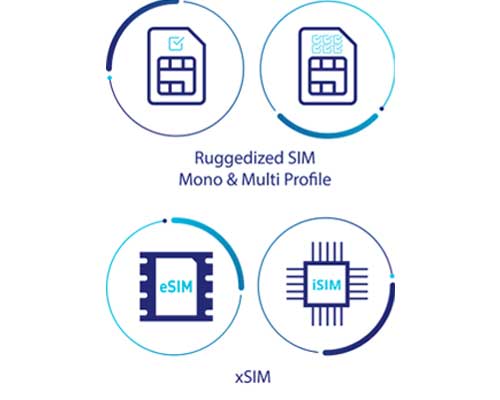
These include the need for robustness, as IoT devices often face extreme environmental conditions, necessitating ruggedised SIMs for durability.
Power efficiency is also critical since these devices usually operate on batteries and are expected to have a long service life.
Space is also a consideration; efficient design and a simple Bill of Materials are important for cost-effective, large-scale manufacturing.
Reliability is non-negotiable, as IoT devices must function reliably over extended periods without human oversight.
Lastly, a strong supply chain is needed to counteract potential chip shortages and maintain consistent production.
At Thales, we know this stage is critical, as it lays the groundwork for an IoT infrastructure capable of enduring the complexities of modern digital ecosystems.
Our expertise ensures that devices are built to last and designed flexibly to adapt to evolving technological landscapes.
By embedding advanced eSIM and iSIM technologies, Thales equips devices with secure, scalable, and efficient connectivity, ensuring a strong foundation for the vast array of IoT applications set to define our future.

Thales Ruggedized IoT SIM and eSIM - Product range overview
Discover our dedicated SIM and eSIM portfolio for the IoT, the preferred solution for enabling secure cellular IoT connectivity.
The Run Phase: Streamlining for Success
OEMs and vendors face a series of complex challenges during the Run phase.
Key among these is equipping devices with the ability to perform critical functions such as eSIM profile downloads without external help. Achieving immediate connectivity post-manufacturing is crucial for smooth operation.
We know that managing the logistical maze of multiple SIM SKUs for different telecom operators can be costly and complex, too.
Requirements also include tackling the regulations against permanent roaming, addressing the intricacies of traditional M2M eSIMs, and avoiding the limitations of low-power cellular technologies.
In this phase, Thales's strategy pivots towards optimising the supply chain and operational processes to ensure efficiency in IoT operations.
This phase is about delivering seamless, trouble-free experiences from production to deployment.
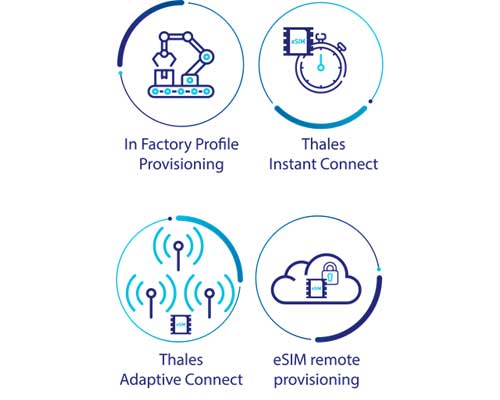
By leveraging eSIM and iSIM's remote provisioning capabilities, Thales eradicates traditional logistical complexities, enabling devices to connect and communicate effectively upon activation. This proactive approach enhances the operational workflow and contributes to significant cost reductions, driving success in the fast-paced world of IoT

Thales Instant Connect
eSIM provisioning connectivity service for the IoT

Thales Adaptive Connect
eSIM remote management to address massive IoT deployments

The Protect Phase: Ensuring Resilient Security
Security is a top priority for service providers.
The fast-changing nature of threats and the increased number of connected devices open doors to DDoS attacks, identity theft, and data breaches, highlighting the need for strong protective measures.
OEMs face a tough road in enhancing security efficiently. Traditional security methods are costly and tricky to set up, and software-based defences often fall short.
Stricter digital security laws in regions like Asia, the EU and the US add to the challenge, increasing accountability for IoT providers.
Moreover, companies need to adopt a security by design approach to tackle security issues.
The Protect phase represents is where Thales deploys its deep cybersecurity expertise to anticipate, deter, and combat threats.
This phase ensures that every IoT device fortified by Thales's technology remains resilient against intrusions, maintaining the trust and reliability critical for the longevity and success of IoT deployments in our increasingly connected world.

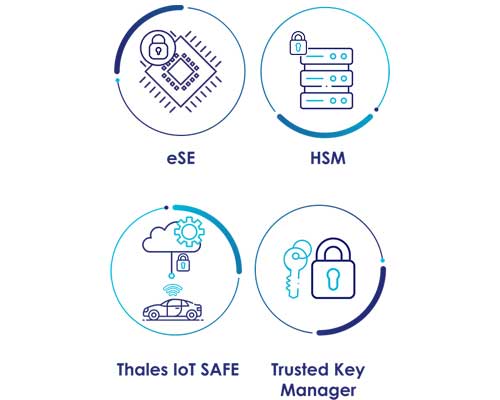
Thales eSE (embedded Secure Elements)
Our tamper-proof hardware is used in devices to enhance security through a secure operating system and applications embedded within a silicon chip.

Thales HSM (Hardware Security Modules)
Our hardware systems safeguard and manage digital keys, perform encryption and decryption functions for digital signatures, strong authentication, and other cryptographic function

Thales IoT SAFE (Addressing IoT security):
Our solution provides an integrated approach to address IoT cybersecurity challenges by utilising secure element technology for device authentication and data integrity.
Thales Trusted Key Manager
Thales Trusted Key Manager handles cryptographic keys across cloud and enterprise environments, ensuring the security and integrity of keys throughout their lifecycle.
Why Thales Stands Apart
It's simple.
We help our customers unleash the transformative power of IoT technologies.
In other words, we support them at every step of the IoT journey with expertise, passion, and innovative solutions that allow businesses to thrive.
Thales's suite empowers mass IoT deployments across sectors, backed by a global presence and partnerships with over 450 connectivity service providers, cementing its market leadership.
What are the key challenges for enterprises when deploying IoT services?
Watch the interview of Thales by Beecham Research, about Thales' approach to the growing IoT market.
Latest Case Studies
Join us at CES Las Vegas 2025
January 7th to 10th 2025 | IoT Pavilion |
Las Vegas Convention Center
At Thales we are shaping a safer and more connected future by delivering innovative solutions that address new threats and evolving regulations and this year we are pleased to be part of CES.
> Don't miss the opportunity to Schedule a meeting with our team to explore opportunities : Thales private meeting at CES 2025 - Registration

EOLO chooses Thales to support drive for universal gigabit broadband Description
EOLO, Italy's leading FWA connectivity provider, is leveraging Thales On-Demand Subscription Manager (OSM) for deploying Fixed Wireless Access (FWA) services, crucial for reaching underserved areas. Thales supports EOLO's goal of universal gigabit broadband, in line with the EU's aim for 1Gbps access for all citizens by 2030. Click the link to learn more!
Read our brochure
Case study: Simplifying IoT deployments
See how Thales simplifies IoT deployments with its IoT Connectivity Platform, featuring Thales Adaptive Connect (TAC) and Thales Connectivity Management. Fully compliant with GSMA eSIM IoT SGP.32 standards, Thales' platform enhances productivity, efficiency, and scalability in massive IoT deployments while ensuring secure, reliable, and straightforward connectivity. Click the link to learn more!
Read our brochure
IoT Connectivity Interview
Join us for an exclusive interview with Thales, the platinum winner at the Smart Cities & IoT Innovation Awards 2024 for eSIM management platform.
Read the interview
IoT Security Interview
Tune into the exclusive interview with Thales, the gold winner at the Smart Cities & IoT Innovation Awards 2024 for the Best IoT Security Solution.
Read the interview
Thales IoT SAFE delivers scalable trust for IoT applications
Infographic
Thales IoT SAFE delivers scalable trust for IoT applications [PDF - 182kb]
Hardware tamper resistant elements deliver scalable trust for IoT applications
Hardware tamper resistant elements deliver scalable trust for IoT applications
Building a connected car we can all trust
An overview of cybersecurity challenges, regulation and best practices
Read our whitepaper
Enabling Secure Connectivity for 5G Fixed Wireless Access to Homes
Read the white paper







